The Growing Risk of Cybersecurity Fragmentation
By Travis Keller, Managing Partner
Chief Information Security Officers (CISOs) are like NFL kickers. Their careers can be defined by a single failure, but successes are rarely celebrated. Of course, a CISO’s job is more difficult than a kicker’s, as they face a moving target — an ever-evolving set of threat actors who strike with seeming randomness and often with impunity. To combat these threats, CISOs spend more than $200 billion each year on information security technologies (1), relying on companies like Microsoft, CrowdStrike, Palo Alto, Okta, Proofpoint and Zscaler to stay a step ahead of bad actors.
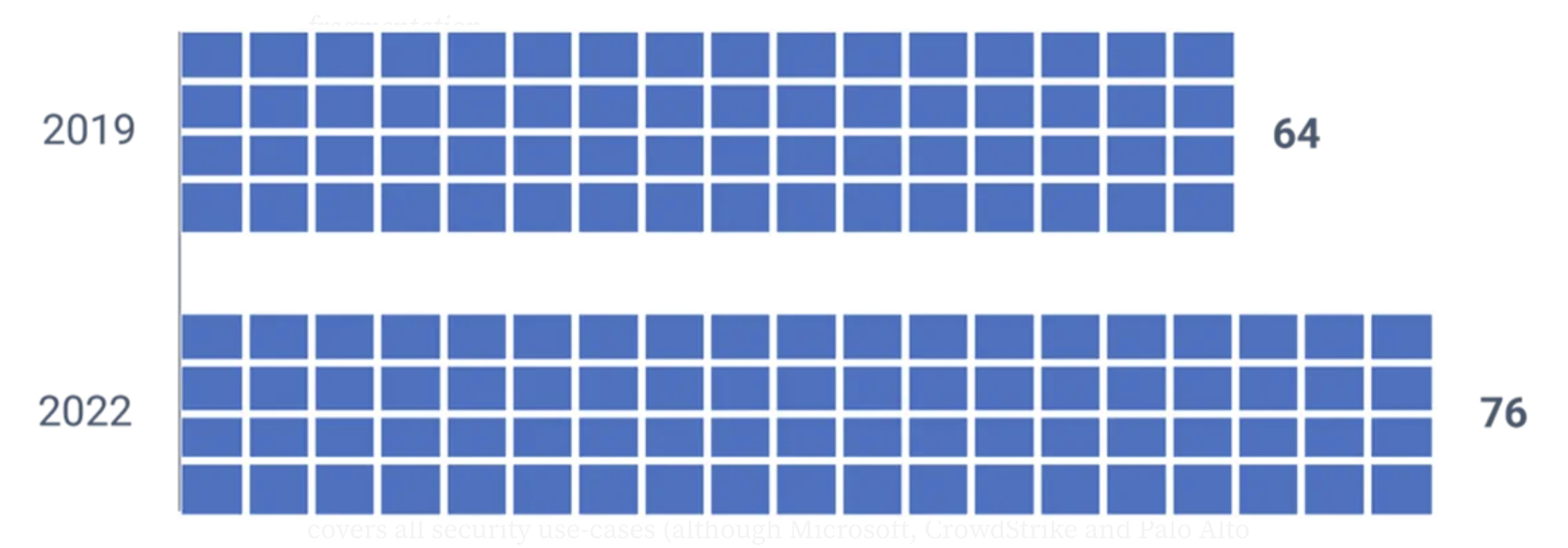
When evaluating the cybersecurity market, and adopting and maintaining relevant tooling, CISOs face yet another challenge: massive fragmentation that drives complexity within business information security technology stacks. In fact, the average enterprise uses more than 75 different security tools (2).
Average number of security tools used by enterprise security teams
(Panaseer Research, 2022)
Evolving information technology and expanding threats are driving fragmentation.
This high level of fragmentation is enabled by two dynamics:
1. Businesses’ attack surfaces are constantly expanding as new data sources, applications, users, networks and clouds offer new entry points for bad actors. And each new nook and cranny can be secured by a group of specialized cybersecurity tools.
2. CISOs often prefer best-of-breed cybersecurity tools to distribute risk and prove their value to Boards. Also, there’s no one-stop-shop vendor that covers all security use-cases (although Microsoft, CrowdStrike and Palo Alto are expanding their coverage).
Momentum Cyber, a leading cybersecurity-focused investment bank, clearly illustrates the fragmentation challenge today’s buyers face with their CYBERscape market map (3), which, by the way, only highlights a small portion of the ~2,000+ cybersecurity technology companies operating today.
Many industries consolidate as they mature, so it’s reasonable to expect that the cybersecurity market may follow a similar course. However, over the next five years, we shouldn’t expect much change. The market will remain fragmented, filled with thousands of providers with less than $10 million in ARR. The reason for this is simple: The pace of evolution is so fast that there is constant demand for new cybersecurity tools on, or near, the edge of technology frontiers. This evolution creates fertile opportunity for new entrants to establish a foothold in one of these niche markets. And as niche markets become mainstream, tools with a foothold become part of best-of-breed security stacks, marketing the importance of a specialized solution with advanced features. As long as IT continues to evolve and cyber threats follow suit, fragmentation will result.
Even resource-rich enterprises are struggling to manage cybersecurity complexities.
The recent hacks on MGM and Caesars demonstrate how evolving IT environments and expanding threats make for challenging cybersecurity risk management. In this attack, a group known as Scattered Spider designed a scheme to hack the slot machines at MGM to rig the results. However, the group soon realized that the slot machine technology was well-protected and not easily manipulated. To salvage their operation, Scattered Spider launched a ransomware attack, ultimately extracting a $15 million payment from Caesars and costing MGM an estimated $100 million during the 10 days it took to bring systems back online (4). This example shows how hackers will adapt to find soft targets, even when most security gaps are filled. As such, CISOs require many solutions to protect an ever-expanding attack surface.
While the current level of market fragmentation supports innovation to secure critical and emerging workloads, it also introduces significant risk in the form of complexity. Consider the complexity of conducting a thoughtful vendor evaluation process for 75 independent cybersecurity tools — let alone the challenge of integrating and monitoring the data feeds from those 75 tools! Even for a 100-person cybersecurity team, this is a tall order. For a small enterprise CISO with a 5-person staff, it’s nearly impossible. Inevitably, the most appropriate tools won’t always be selected and when they are, they’ll likely be used ineffectively. Complexity may create a perception of security, but it also creates risk. We’re witnessing this reality play out across thousands of global enterprises.
To combat the risks of fragmentation, simplification and integration are key.
Cybersecurity fragmentation, and the resulting complexity, is both serious and prevalent, but there are productive paths forward for CISOs. This is where I feel obligated to add a quick disclaimer: I am not a cybersecurity professional. I invest in technology services businesses that help enterprises get the most out of technology. This vantage point, while narrow, provides a clear view into the tangled web of cybersecurity tools that our portfolio companies are often fixing for their customers. For CISOs, productive paths forward include two best practices that can (and probably should) be pursued in tandem:
1. Simplify the cybersecurity stack. CISOs can simplify by trading off features for usability. For example, Microsoft, CrowdStrike, Palo Alto and other vendors are expanding the breadth of their offerings and adding modules to address new threats. These new modules aren’t always the most sophisticated and can draw the ire of some experts who point out key technical shortcomings relative to best-of-breed vendors. But for CISOs who are unable to effectively manage a best-of-breed cybersecurity stack, this might be a valuable trade-off.
2. Engage service providers to improve integration. There is an emerging market of information security service providers that help customers integrate, configure and manage a holistic information security stack. Strong, cyber-focused resellers and service providers maintain teams with specialized expertise that smaller CISO teams can’t match. They’ve also deployed and integrated tools repeatedly, and learned lessons that can benefit security teams of all sizes.
Cybersecurity service providers and integrators have a timely market opportunity.
The growing risk of fragmentation will drive success for service providers interested in helping enterprises simplify technology and cybersecurity environments. Our most recent cybersecurity investment, Consortium Networks, pursues this strategy, offering customers a CrowdStrike-centric security platform that’s complemented by numerous well-integrated point solutions to fill gaps. Similarly, C3 Integrated Solutions helps customers simplify technology and cyber environments by offering the Steel Root Technology Platform, a standard reference architecture-based technology stack with carefully integrated security and compliance tools.
M|C Partners will continue to seek out and support companies executing on business models supported by this same thesis. If you’re an integrator or service provider working to help enterprises grapple with cybersecurity fragmentation and complexity, we’d love to hear from you.
Sources:
(2) https://panaseer.com/reports-papers/report/2022-security-leaders-peer-report/
(3) https://momentumcyber.com/docs/Monthly/Cybersecurity_Snapshot_August_2023.pdf
(4) https://slate.com/technology/2023/10/mgm-caesars-casinos-vegas-hacks-ransomware-gambling.html